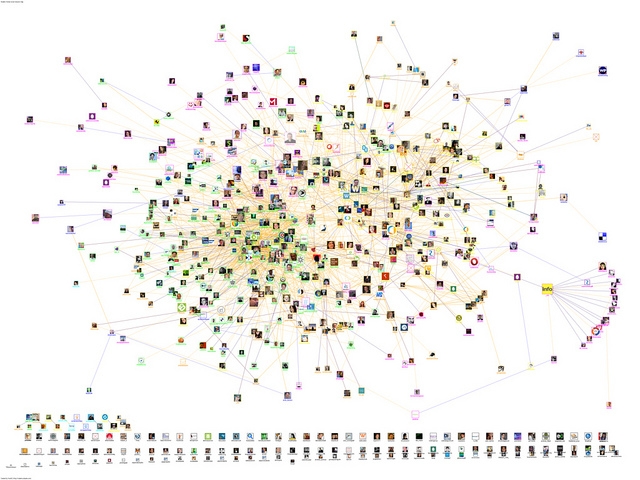
Social Network Analysis (SNA) methods are the subject of this first blog in a series of blogs on analytics techniques, with the discussion focused on several question constructs, as per my previous foundation blog on the wider Analytics topic:
- What data are we performing the analysis on?
- Why are we performing this type of analysis?
- Who are we trying to identify with the analysis?
- What benefit does this analytics technique give us on the chosen data set?
- How can we make use of the result set produced by these analytics?
The intention is not to directly answer each question, but to discuss SNA as applied to the problem domain of understanding intercepted communications data, and more specifically the actors performing those communications and their intent.
You’ll be able to infer the answers, which will be quite apparent from the following discussion, to the questions above.
The problem domain space to which we will apply SNA for this blog is communications interception. This encompasses both IP communications, which can be characterized by IP data records (IPDR) containing metadata about protocols used, time of communication, end points (party A, B …. N), etc., and voice communications from traditional circuit switched or mobile networks, which can be characterized by Call Detail Records (CDR) containing similar data to IPDRs. Typically, surveillance of modern communications networks yields more discrete IPDR and CDR session data per user, as available bandwidth increases due to technology advancements such as LTE, and user behavior changes to generate more data driven by ‘Apps’ on mobile devices.
The consequence of this is that Analysts have significantly more data to sift through for that piece of actionable intelligence, or pattern of behavior, that would drive their investigations forwards. Added to this variable is the multiplicity of identities that each physical user now collects as a standard part of their interaction with both Voice and IP networks. It is not uncommon for normal users to have 5 or more email addresses, several fixed and mobile phone numbers or VoIP identities and a number of application identities too – and these users are not intentionally trying to obfuscate or hide their communications – it’s just a natural consequence of the network interaction.
Now consider the criminal user of the network – who is trying to obfuscate their communication using multiple and often changing phone numbers and cyber identities, and the problem is clear. How do we resolve all of those esoteric, dynamic identities and make them attributable to a physical person, such that we can discover their intent and potentially other actors in the networks that we may want to monitor? This is where SNA is key in the problem domain. Specifically, when SNA is coupled with an identity management tool, it enables communications networks (or graphs) to be collapsed in complexity to discover the intent of the actors under surveillance.
This collapse is achieved by collating known identities of a subject of interest (SOI) in to the identity management tool, so that the identities are attributable to a physical entity (this could be a person or group of people, i.e. modeling the intent of a criminal organization). Once physical identity has been attributed to a number of communications identities, that understanding can be applied to a communications graph. This enables the Analyst to collapse many hub and spoke topologies of communications from discrete communications identities to a multiplicity of endpoints, into a more concentrated hub and spoke topology of communications. The collapsed graph essentially shows the true communication between the physical parties, and this highlights intent between those parties, which was fragmented and almost impossible to understand in the original communications graph.
Once the Analyst has gained this understanding, it allows them to deduce the true volume of communications between the physical entities in the communications graph, and how significant that may be for each of the media types presented (email, VoIP, Voice, etc.). This is all accomplished using metadata about the communications. Once a specific criminal intent is discovered using the methodology discussed above, the Analyst then has the ability to set up intercepts on some of the remote identities that the SOI was communicating with or look at the current intercepted product data for the SOI and move their investigation to the next phase. This reconstructs the Voice or IP streams into the session data as experienced by the SOI under surveillance.
The beauty of this type of analysis is that it can evolve as the understanding of the SOI changes over time, which means the analysis can evolve too, as new phone numbers, email addresses and other communications identities are attributed to the SOI (i.e. they buy a new disposable phone or join a new email service, but that phone/email address exhibits the same communication pattern with endpoints). The other benefit is that the presentation of the data is visual, enabling the Analyst to focus in on the data gateways (physical entities which represent multiple communication identities in the communication graph) as they become evident in the SNA, and even explode those gateways to see the multiple identities currently attributable to them, and the pattern of behavior exhibited as part of those identities. This is incredibly useful, as many SOIs segment their activities, using different communications identities for their illicit behavior as opposed to their day to day activity (such as emailing a spouse) – and they are less likely to change those personal channels – so they act as a perfect baseline/signature to keep track of a suspect in the communications domain.
In summary, this particular application of SNA against intercepted communications data can be considered an intermediary step towards gaining actionable intelligence when building an investigation profile around an SOI. It is not however, the start of the analysis methodology. For that we need to look at Grid Analysis of metadata, which will be the subject of the next blog in this series.
About SS8 Networks
SS8 provides Lawful Intelligence platforms. They work closely with leading intelligence agencies, communication providers, law enforcement agencies and standards bodies and their technology incorporates the methodologies discussed in this blog. Xcipio® is already proven to meet the very high demands of 5G and provides the ability to transcode (convert) between lawful intercept handover versions and standard families. Intellego® XT natively supports ETSI, 3GPP and CALEA handovers, as well as national variants. Intellego XT’s MetaHub component is a best-in-class data analytics tool. Both product portfolios are used worldwide for the capture, analysis and delivery of data for the purposes of criminal investigations.