Cell site simulators (CSS) are an important tool used by law enforcement around the world to track down fugitives, find missing persons and to investigate or prevent serious crimes. In the fifth generation of mobile (5G), changes have been made to protect subscriber privacy and to limit the effectiveness of cell site simulators. This article will explain how, when 5G is fully implemented, those changes will block or severely limit the CSS mission. We will also describe the approaches available to law enforcement to address the impacts.
A CSS a portable device which has some of the componentry of a mobile network. The CSS presents itself as a preferred, legitimate tower of a mobile network operator (MNO). Mobile phones (a.k.a., user equipment or UE) are, by design, always optimizing for the best user experience and will naturally connect to the CSS’ much stronger and preferred signal. In identifying itself to the network, the UE provides its permanent identifier and it does so in the clear. Protecting the permanent identifier was one of the major improvements in subscriber privacy on 5G.
On 4G networks, the permanent identifier was the international mobile subscriber identity (IMSI). In 5G the permanent identifier is called the Subscription Permanent Identifier (SUPI) and it contains the IMSI. In 5G, the IMSI is encrypted and is combined with information about the home network to create a Subscription Concealed Identifier (SUCI). The SUCI (not SUPI) is sent over the air. Deep within the 5G mobile core, the network can decrypt the SUCI into the SUPI.
The Impact of 5G on Cell Site Simulator Missions
When looking to locate a UE (for example, in a missing person case), the CSS operator will typically know the IMSI. On 4G and earlier networks, the UE would provide its IMSI in the clear, letting the CSS operator know if the UE is in the area. The antenna to which the UE connects provides a direction in which to search. Signal strength provides range. On 5G networks the SUCI is provided but it is a scrambled form of the IMSI, making it nearly impossible to associate with the missing person.
When looking to determine who is at a location (for example, who is in a residence before a breach team enters), the CSS operator will need to collect the IMSIs and associated signal strength. By overlaying multiple readings from multiple perspectives, the location of a UE within the residence can be estimated. On 5G networks, the SUCI cannot be compared to known IMSIs or looked up in databases to know which individuals are inside. Furthermore, the SUCI is re-scrambled each time that the UE is asked to identify itself making it impossible to know the true count of UEs within the residence or to estimate the locations or the UEs with the residence.
When Will Law Enforcement Feel the Impact?
The end game for MNOs adopting 5G is to have an all-5G network. The path to an all-5G network looks different if the MNO has an existing 4G network or is a new 5G MNO or even a private 5G network. Existing 4G MNOs are taking a multi-phased approach. In the first phase, the MNOs offer new 5G UEs that connect over the new 5G radio network to the existing 4G mobile core (EPC). In this phase, 5G UEs behave just like 4G UEs, causing no impact to the CSS mission. The second phase for existing 4G MNOs is the addition of a 5G mobile core (5GC). Most 5G MNOs began the first phase 2-3 years ago and will roll out their 5GC in upcoming months. Once complete, the CSS mission will be severely impacted or outright blocked.
SS8 Provides an ETSI-Compliant Solution
The European technical standards institute (ETSI) has released a framework, built on top of the ETSI lawful intercept architecture for SUPI resolution. As a leading supplier of standards-compliant lawful intercept solutions, SS8 has already added support for the ETSI framework.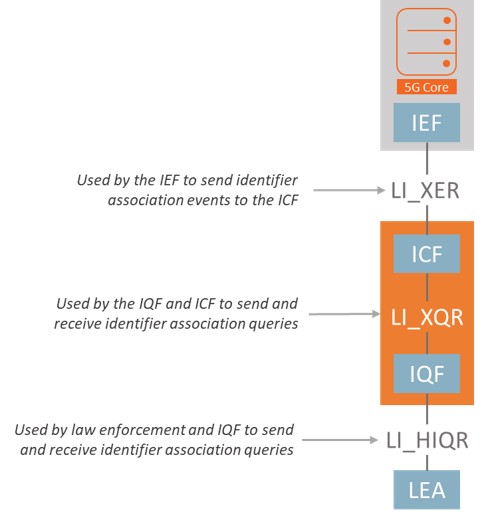
The ETSI-based approach introduces three functional elements to the lawful interception architecture:
Identity Event Function (IEF) detects changes in identifiers and provides those changes in the form of identifier association event records to the ICF;
Identity Caching Function (ICF) caches identifiers provided by the IEF and answers queries that originate from the IQF; and,
Identity Query Function (IQF) handles and responds to real-time requests for identifier associations in the form of queries by law enforcement agencies (LEAs). This is illustrated to the right.
This framework allows for law enforcement to issue queries against one or more SUCIs and to respond with a SUPI. In this model, SS8 provides the ICF and IQF. The IEF is supplied by the 5G mobile core network equipment vendor.
SS8 Provides a 3GPP-Based Solution
SS8 has worked with law enforcement, telecom operators and leading CSS vendors to develop an alternative approach. This approach leverages the 3GPP standards and does not require for the mobile network core software to be upgraded or scaled. The solution works with any 3GPP compliant network equipment vendor, making it vendor agnostic.
The solution balances the real-time nature of the CSS mission with the integrity and security precautions required of telecom operators. And, the solution is built upon the SS8 mediation platform, used daily around the world to comply with lawful intercept regulations – providing the oversight and security procedures expected for such a sensitive mission.
For more information, please contact SS8 sales.
 About Kevin McTiernan
About Kevin McTiernan
Kevin has over 20 years of extensive experience in the telecommunications and network security industries. At SS8, Kevin is the VP of Government Solutions and is responsible for leading the vision, design, and delivery of SS8’s government solutions, including the Xcipio® compliance portfolio. You can learn more about Kevin on his LinkedIn profile by clicking here.
About SS8 Networks
SS8 provides Lawful Intelligence platforms. They work closely with leading intelligence agencies, communication providers, law enforcement agencies and standards bodies. Their technology incorporates the methodologies discussed in this blog and the Xcipio® and Intellego® XT product portfolios are used worldwide for the capture, analysis, and delivery of data for the purposes of solving criminal investigations.



